For the PenTest+ certification exam, remember the difference between active and passive information gathering. Active information gathering involves engaging with the target environment, such as via scans, while passive information gathering involves using public internet resources to discover information about the target without being detected.
Many of the active information gathering techniques involve scanning target systems to find out things like the operating system that is running and the services running on the system.Domain name system (DNS) profiling involves sending queries to DNS servers to retrieve information on the systems that might exist within the company, such as a mail server or a web server. Keep in mind that in passive information gathering you were able to obtain the DNS server information for a company by doing a Whois lookup. The next step is to send queries to those servers to find out what DNS records exist.
You can use a number of tools to perform DNS profiling. The two most common are the commands nslookup and dig.
nslookup
nslookup is a TCP/IP command in Windows and Linux that allows you to query DNS servers for different types of DNS records. You can use nslookup as a command or as an interactive prompt where you type nslookup commands into the prompt. Here is an example of using nslookup as a regular command to retrieve the internet protocol (IP) address of a host:nslookup www.wiley.com
www.wiley.com. In this example, four IP addresses answer the FQDN.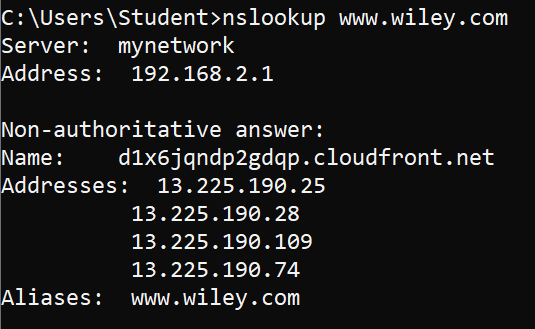 Using nslookup to resolve an FQDN to an IP address
Using nslookup to resolve an FQDN to an IP addressWith nslookup you can also do things like specify you want to see the email servers for a company by setting the type of query to MX (mail exchange) records. To do this, use the following commands:
nslookup
set type=MX
wiley.com
wiley.com has four mail servers. When performing the pentest, you would document the four FQDNs of the mail servers and then resolve those to IP addresses by using nslookup <fqdn>.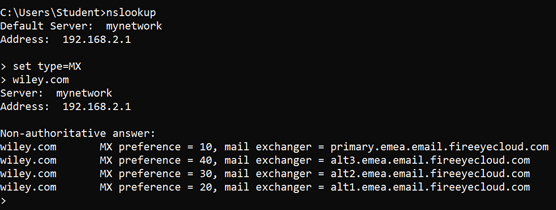 Using nslookup to locate mail servers
Using nslookup to locate mail serversAs one final example, you can try to retrieve all of the DNS records for a particular company by doing a DNS zone transfer. DNS zone transfers should be controlled by the server administrators, so if you are successful, you definitely want to make a note of it and add it to your remediation list in the pentest report.
To attempt a zone transfer from Windows using nslookup, use these commands:
nslookup
server <ip_or_fqdn_of_company_DNS_server>
set type=all
ls -d <company_domainname>
wiley.com (which it is not), you could use the following commands to do a zone transfer:
nslookup
server 192.168.1.1
Set type=all
ls -d wiley.com
dig
dig, which is short for Domain Information Gopher, is a command in Linux used to perform DNS profiling. I like the output of dig a bit better than the output of nslookup because I think it's easier to read.To find out the IP address of www.wiley.com, type the following command on a Kali Linux machine:
dig www.wiley.com
www.wiley.com, and the answer section is listing the four IP addresses associated with it.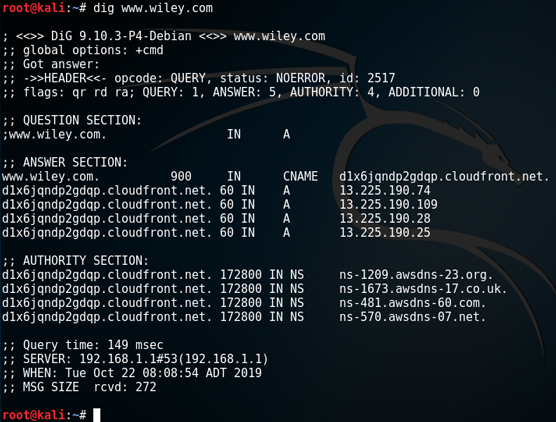 Using dig to query DNS
Using dig to query DNS
What I like about dig as a command is that you can ask for the short version of the output by adding +short to the command. For example:
dig www.wiley.com +short
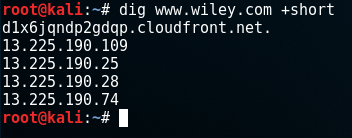 Adding
Adding +short in dig keeps the output clean.If you want to use dig to retrieve specific records, such as MX records to find out the email servers for a company, you could use the following command:
dig wiley.com MX
+short to that command:
dig wiley.com MX +short
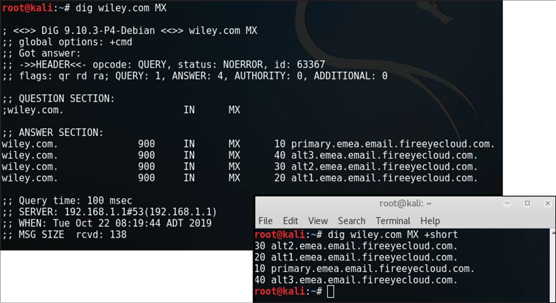 Retrieving the email server list with dig
Retrieving the email server list with digIf you want to do a zone transfer with dig to attempt to retrieve all of the DNS records that exist, you could use the following dig command:
dig wiley.com axfr
You may notice that you do get a few records that identify the DNS servers for the company (NS) and also a few host records (A); however, you may also notice that at the bottom of the output it says “Transfer Failed.” This is because the server administrators for that company are blocking full zone transfers as it exposes too much information to the hacker. If you are testing a company and zone transfers are not refused, you want to be sure to document that in your pentest report.
For the PenTest+ certification exam, know that dig and nslookup are two tools that can be used to perform DNS profiling to help identify hosts that exist within an organization.






